A group of notorious North Korean hackers were able to steal $3 billion worth of cryptocurrencies from users by creating a fake blockchain game, a cybersecurity firm reported yesterday. Kaspersky Lab said The Lazarus Group exploited a key vulnerability in the Google Chrome browser, which allowed them to drain their victims’ crypto wallets.
Lazarus Group: $3 Billion Crypto Heist
It was reported that North Korean hackers used a fake game to steal more than $3 billion in cryptocurrencies – an operation the group successfully carried out within a six-year period from 2016 to 2022.
This theft is an adverse consequence of Google’s failure to fix the vulnerability in the Chrome browser.
Meanwhile, a blockchain detective conducting a separate investigation found that Lazarus Group Carried out 25 hacking attacks, laundering $200 million worth of cryptocurrency.
It also revealed the existence of a network of developers in North Korea who work for “established” cryptocurrency projects. The network reportedly receives a monthly salary of $500,000.
Questionable game plan
Kaspersky Labs analysts Vasily Berdnikov and Boris Larin said that Lazarus Group created a fake game called DeTankZone or DeTankWar that revolves around non-fungible tokens (NFTs) to steal the crypto wallets of its victims.
Analysts reveal hackers used zero-day Vulnerability in Chrome browser In their dishonest act.
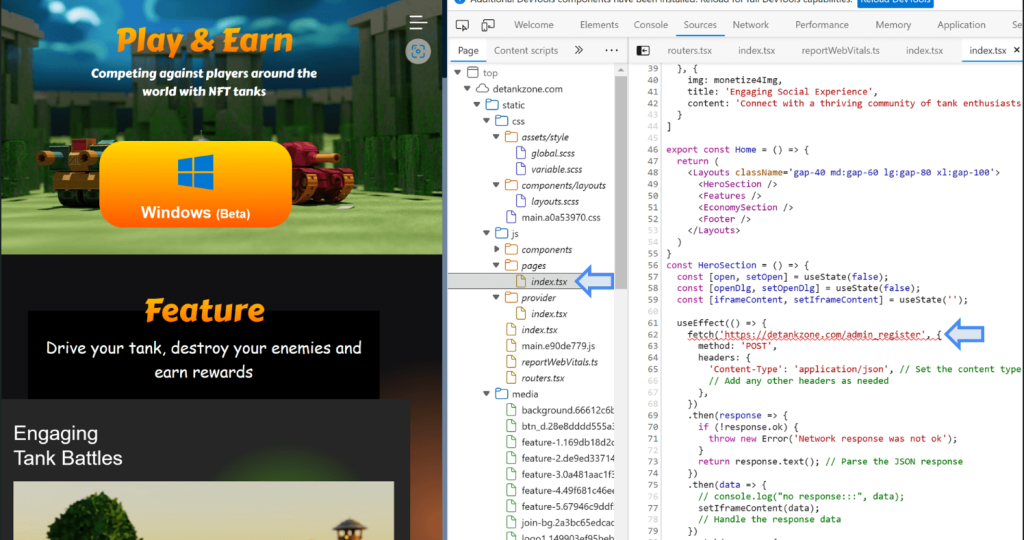
Website appearance and the hidden exploit loader. Source: Kaspersky Lab
Berdnikov and Larin reported that the hackers used a fake game to persuade their victims and lead them to a malicious website that injected malware, called a manuscript, into their computers.
Using the script, hackers were able to corrupt Chrome’s memory, allowing them to obtain users’ passwords, authentication tokens, and everything else they needed to steal their unwitting victims’ crypto.
12 days to solve the problem
Kaspersky Lab analysts discovered what Lazarus Group was up to in May. Berdnikov and Larin immediately reported the issue to Google so the platform could fix the vulnerability.
However, Google was unwilling to address the zero-day vulnerability problem by taking them 12 days to fix the vulnerability.
Boris Larin, a leading security expert at Kaspersky Lab, said that the remarkable effort put in by the hacker group in the said hacking campaign indicates that the group has an ambitious plan.
Larin said what the group has done may have a broader impact than previously thought.
Lazarus Group is a reminder that the fight against hackers continues. The Chrome vulnerabilities highlight that platforms should always ensure their security measures are up to date and remain vigilant against cybersecurity threats.
Featured image from Le Parisien, chart from TradingView












